Vulnerability Report - September 2025
Introduction
This vulnerability report has been generated using data aggregated on Vulnerability-Lookup, with contributions from the platform’s community.
It highlights the most frequently mentioned vulnerability for September 2025, based on sightings collected from various sources, including MISP, Exploit-DB, Bluesky, Mastodon, GitHub Gists, The Shadowserver Foundation, Nuclei, SPLOITUS, and more. For further details, please visit this page.
The Month at a Glance
September 2025 has been marked by a diverse set of vulnerability sightings across multiple platforms and software ecosystems. The data collected through Vulnerability-Lookup indicates that both newly disclosed and previously known vulnerabilities continued to see active exploitation and discussion in the wild.
CVE-2025-10585, affecting Google Chrome, dominated the reports with 94 sightings. Other frequently sighted vulnerabilities include CVE-2025-10035 in Fortra’s GoAnywhere MFT and CVE-2025-42957 in SAP S/4HANA, both of which reflect persistent enterprise-level risks. These instances underscore the continued need for rapid patch deployment and robust monitoring in enterprise environments.
Network and infrastructure devices also remained a focus for adversaries. Vulnerabilities such as CVE-2023-51767 in OpenSSH and several router-specific CVEs like CVE-2017-18368 highlight the ongoing relevance of securing network endpoints against unauthorized access and exploitation. Similarly, Linux-based vulnerabilities, including CVE-2024-50264, accounted for a significant number of sightings, reinforcing the importance of kernel updates and system hardening practices.
From a severity perspective, most sightings fell into the High and Critical categories, with VLAI confidence scores often exceeding 0.95. This aligns with global observations of attackers prioritizing high-impact targets, such as widely used browsers, enterprise software, and critical network infrastructure. For example, Adobe Commerce, Sitecore Experience Manager, and Microsoft Entra were all associated with vulnerabilities of critical severity, underlining the necessity for organizations to prioritize patching and risk mitigation.
September 2025 reinforces several key trends in the cybersecurity landscape: high-severity vulnerabilities remain prevalent across browsers, enterprise software, and networking devices; unpublished vulnerabilities are actively exploited; and community-driven data aggregation plays a critical role in timely awareness and response. Organizations are encouraged to review patch management processes, monitor community sightings, and leverage threat intelligence feeds to mitigate exposure to these ongoing threats.
This month’s report features a new section dedicated to Known Exploited Vulnerabilities catalogs.
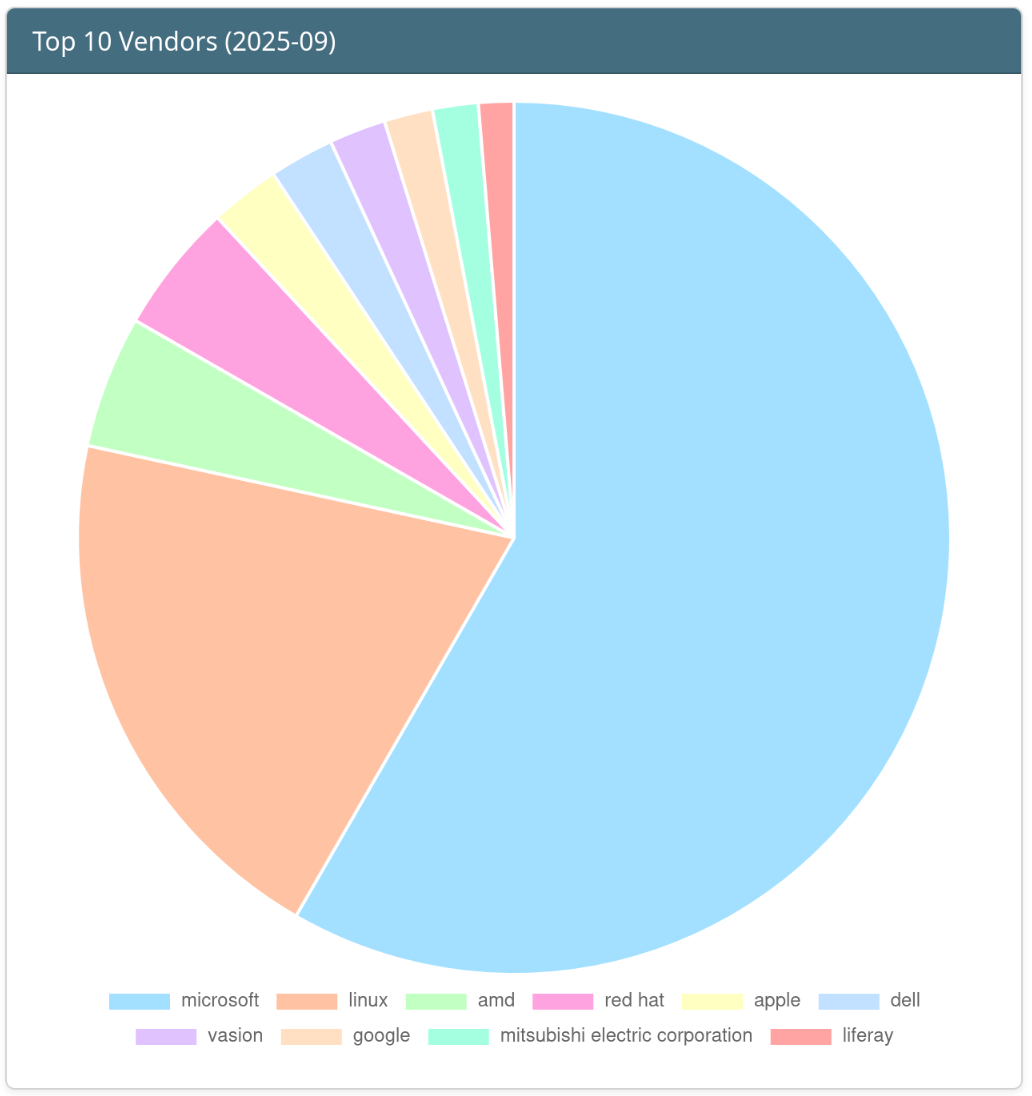
Top 10 Vendors of the Month
Top 15 vulnerabilities of the Month
Known Exploited Vulnerabilities
New entries have been added to major Known Exploited Vulnerabilities catalogs.
CISA
ENISA
| CVE ID | Date Added | Vendor | Product | VLAI Severity |
|---|---|---|---|---|
| CVE-2025-25231 | 09/09/25 | Omnissa | Omnissa Workspace ONE UEM | High (confidence: 0.8877) |
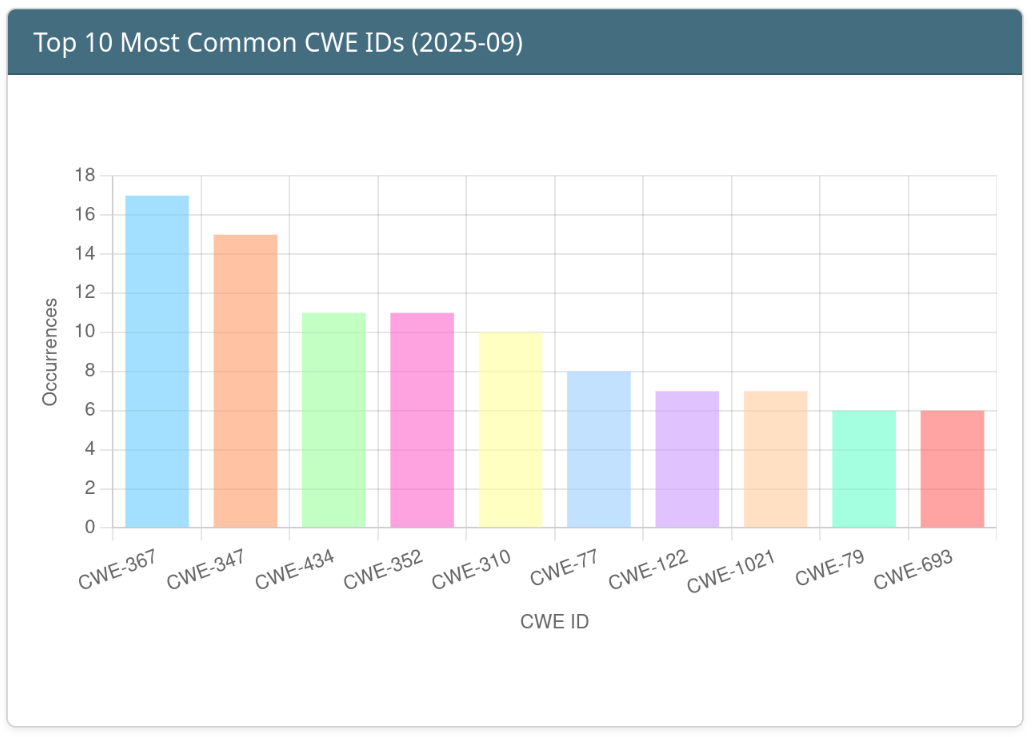
Top 10 Weaknesses of the Month
Click the image for more information.
Ghost CVE Report
A ghost CVE is a vulnerability identifier that’s already popped up in the wild but is still listed as RESERVED or NOT_FOUND in official registries like NVD or MITRE.
Sightings detected between 2025-09-01 and 2025-09-30 that are associated with unpublished vulnerabilities.
Continuous Exploitation
- CVE-2024-28995 - SolarWinds Serv-U
- CVE-2023-42344
- CVE-2019-1653 - Cisco Small Business RV Series Router Firmware
Insights from Contributors
- SAP Security Patch Day - September 2025
- npm.js - account qix and duckdb_admin compromised and associated CVEs allocated
- Cisco AnyConnect/ASA - vulnerabilities
- Subverting code integrity checks to locally backdoor Signal, 1Password, Slack, and more
Thank you
Thank you to all the contributors and our diverse sources!
If you want to contribute to the next report, you can create your account.
Feedback and Support
If you have suggestions, please feel free to open a ticket on our GitHub repository. Your feedback is invaluable to us!
https://github.com/vulnerability-lookup/vulnerability-lookup/issues/
Funding

The main objective of Federated European Team for Threat Analysis (FETTA) is improvement of Cyber Threat Intelligence (CTI) products available to the public and private sector in Poland, Luxembourg, and the European Union as a whole.
Developing actionable CTI products (reports, indicators, etc) is a complex task and requires an in-depth understanding of the threat landscape and the ability to analyse and interpret large amounts of data. Many SOCs and CSIRTs build their capabilities in this area independently, leading to a fragmented approach and duplication of work.
The Computer Incident Response Center Luxembourg (CIRCL) is a government-driven initiative designed to provide a systematic response facility to computer security threats and incidents. The organization brings to the table its extensive experience in cybersecurity incident management, threat intelligence, and proactive response strategies. With a strong background in developing innovative open source cybersecurity tools and solutions, CIRCL’s contribution to the FETTA project is instrumental in achieving enhanced collaboration and intelligence sharing across Europe.